Protects Your Business
Protects Your Assets
Protects Your Customers
Gain Peace Of Mind
Cyber threats are evolving
Cyber attacks are increasingly sophisticated and frequent, hitting businesses where it hurts most in their operational continuity and financial security.
In light of the evolving threat landscape, we’ve had to shift our mindset. We no longer believe it’s a question of if you’ll be targeted, it’s now a question of when.
That’s why we focus on proactive cybersecurity measures that not only protect your business operations but also align with your growth strategy, turning technology into an asset, not a liability.


Why Outsource Cybersecurity?
Outsourcing your cybersecurity needs to experts in the field ensures that your systems are constantly monitored, updated, and protected against emerging cyber threats. This frees up your team to focus on core business operations while enjoying peace of mind about your cybersecurity posture.
Why Choose My Tampa IT?
Choosing My Tampa IT as your cybersecurity partner provides a cost-effective, comprehensive approach to protecting your data. We bring specialized expertise, advanced tools, and a dedicated team—ensuring uninterrupted, top-tier security that evolves with your business needs.
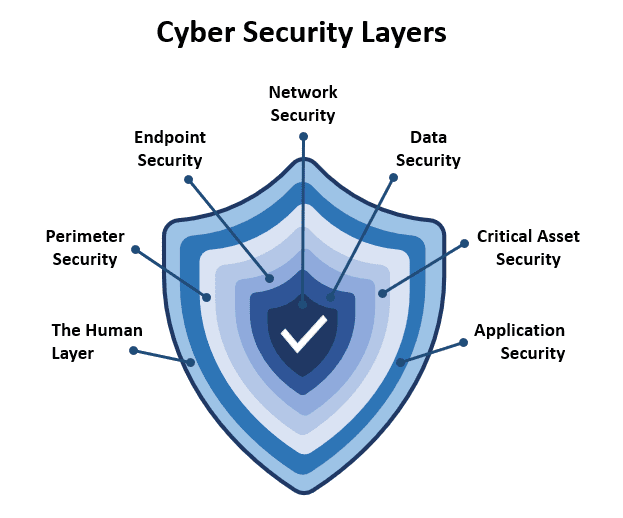
Network Security
Protect The Foundational Elements Of Your Business’s Digital Environment From Unauthorized Access, Data Theft, And Infrastructure Damage.
Network Security
Implement state-of-the-art solutions to protect your network from unauthorized access, data theft, and potential infrastructure damage.
Firewall Management
We configure and manage your firewalls to control network traffic, bolstering your defenses against unauthorized access and cyber threats.
VPN Services
Secure your remote connections to company networks with VPN services, ensuring data encryption and identity verification from any location.
Endpoint Security

Safeguard All Endpoint Devices, Such As Laptops, Servers, And Mobile Devices To Secure Your Network Against Multiple Types Of Cyber Threats.
Endpoint Protection
Defend all endpoint devices, from laptops to servers, providing a robust security layer against various cyber threats.
Endpoint Detection And Response (EDR)
Monitor end-user devices to detect and respond to cyber threats like ransomware and malware.
Mobile Device Management
Centrally manage and secure company-owned and personal mobile devices, ensuring they meet compliance standards and security protocols.
Threat Detection and Response
Implement real-time solutions for detecting and neutralizing threats, ensuring your digital assets are continuously monitored and secure.
Communication Security
Share your communication channels from a range of cyber threats to keep both international and external interactions secure
Email Security
Advanced email filters and scans intercept phishing attempts, malware, ransomware, and other cyber threats before they reach your employees’ inboxes.
Secure File Sharing
Secure your file transmissions both within and outside your organization, ensuring all data is encrypted and authenticated.
Employee Education and Training
Data Security and Encryption
Implement robust measures to secure the transfer and storage of your data, protecting it both in transit and at rest.
Data Encryption
Protect your critical data by rendering it unreadable to unauthorized users, securing it both at rest and in transit.
Email Encryption
Safeguard sensitive information, ensuring your emails are only readable by the intended recipients.
Secure File Sharing
Secure your file transmissions both within and outside your organization, ensuring all data is encrypted and authenticated.
Application Security
Control application installations and access protocols to ensure that only authorized users interact with your system, reducing the risk of compromise.
Multifactor Authentication
Enhance your security protocols by requiring multiple forms of verification before granting access, reducing the risk of unauthorized entry.
Application Whitelisting
Allow only pre-approved applications to run on your network, effectively reducing the attack surface for malware and unauthorized software.
Policy Enforcement
Enforcing application policies enhances your organization’s overall security and system integrity.
Remote Work and Mobile Device Management
Manage and secure mobile and remote devices to meet compliance standards and maintain robust security protocols, whether in the office or working remotely.
VPN Services
Secure your remote connections to company networks with our VPN services, ensuring data encryption and identity verification.
Remote Control
Remotely access your work computer from anywhere, using a secure application. It’s as if you were right at your desk.
Mobile Device Management
Centrally manage and secure company-owned and personal mobile devices, ensuring they meet compliance standards and security protocols.
Vendor and Third-Party Management
Minimize risks associated with external entities having access to your network by evaluating and securing third-party relationships.
Financial Risk Mitigation
Guard your financial well-being by preemptively addressing cyber risks
Are you certain your business would survive a cyber-attack?
A Cybersecurity Risk Assessment offers a comprehensive overview of an organization’s current cybersecurity posture and whether there are areas for improvement.
It is an excellent tool for uncovering, addressing, and neutralizing potential weak spots in your cybersecurity framework so that you can prioritize and address any vulnerabilities.
With our assessment, you’ll learn:
• Whether cybercriminals are aware of your organization today
• If you are actively being targeted
• How well your current network, technology, and team would withstand a cyberattack
• Your overall cybersecurity risk profile—and so much more.
We’ll pinpoint any security gaps and deliver a comprehensive report, complete with an actionable remediation plan that outlines recommended steps for improvement. Make informed decisions, boost your defense strategy, and gain peace of mind.
Why Outsource Cybersecurity?
Outsourcing your cybersecurity offers several key advantages.
Expertise!
You get access to a broader range of expertise without the overhead costs of hiring full-time specialists. This is especially critical for cybersecurity, where the threat landscape is constantly evolving.
Tools!
We bring tools and solutions that are often too cost prohibitive and out of reach for small-medium size businesses.
Focus!
An outsourced team can focus entirely on cybersecurity, freeing up your in-house staff to concentrate on core business activities.
Scalable!
We are a scalable solution, able to grow with your company’s needs.
Cost effective!
You get an entire team of cybersecurity pros, for the fraction of adding just one in-house person to your team.
Availability!
Everyone needs time off. What happens when your hard-working IT person goes on vacation or must take a sick day? With My Tampa IT, our whole team is here for you.
Resources!
Have a large project that takes multiple people? We have the hands you need.
Choosing My Tampa IT as your cybersecurity partner provides a cost-effective, comprehensive approach to protecting your data. We bring specialized expertise, advanced tools, and a dedicated team—ensuring uninterrupted, top-tier security that evolves with your business needs.

Client Testimonial
“We were lucky to find My Tampa IT when we moved our family company to Florida. My main concerns were hacking and cyber security. There is proof in their process, and they go above and beyond to ensure your company is protected. It may not be the cheapest company out there, but you really do get what you pay for. They are the BEST company to work with. If I could give 10 stars, we would!”
– Manufacturer, Owner